How does extending the Security Council cohort duration from 1 year to 2 years impact voter engagement and accountability
I’m supportive of all the proposed changes outlined in this AIP. These improvements strike the right balance between reducing operational burden and increasing inclusivity, while keeping the process secure and aligned with the DAO’s needs.
I’ll be voting in favor of all the changes.
The following reflects the views of the Lampros DAO governance team, composed of Chain_L (@Blueweb) and @Euphoria, based on our combined research, analysis, and ideation.
Thank you, @Arbitrum, for the clarifications on the questions.
We are voting FOR the following options in the Snapshot voting: Increase cohort duration, Reduce qualification threshold, Allow candidates to rotate keys, and Allow members to rotate keys.
One election per year with two-year terms reduces fatigue and gives more time for real review. Lowering the nominee threshold to 0.1% of Votable Tokens should widen the pool while keeping standards in the final round. Letting candidates rotate keys during the compliance stage fixes a practical risk before voting starts. Letting members rotate keys during their term, with the 18-day governance path, replaces ad-hoc non-emergency actions with a clean and visible process. Forum notes on submitted rotations and short follow-ups after execution provide enough visibility without exposing sensitive procedures.
We are not voting in favour of: Allow members to bypass Nominee Selection. We appreciate the intent to reduce overhead for incumbents. Our preference is to keep a small, fresh signal of community support each cycle, so we are not supporting the full bypass as we mentioned before. A light continuity check and a short-term summary from incumbents would keep accountability in place while preserving most of the simplicity you’re aiming for. If the final on-chain version reflects that balance, we are comfortable moving to support.
We voted for the proposals within this snapshot, except for “Allow members to bypass Nominee”.
In our view, extending cohort duration and lowering thresholds will both strengthen governance continuity and allow more diverse candidates to participate. The introduction of key rotation mechanisms is another critical step forward, as it reduces operational risks and ensures Council members remain responsive.
However, we remain unconvinced by the bypass of the Nominee phase for current members. It is better to seek renewed legitimacy from the DAO even for existing members, and the proposed change didn’t seem necessary.
Overall, the package of changes represents meaningful progress, and we are glad to support it in nearly all respects.
Given our experience in governance, our relationship with Arbitrum, and our previous application to the Security Council, we see these changes as a good step to reduce operational overhead by introducing longer terms, encourage participation, and strengthen security (Key Rotation just for members).
On one hand, we don’t see a major issue with having only a few candidates, since most bring strong alignment with Arbitrum and the skills needed for the role. Furthermore, the clarifications shared here should help drive broader participation.
On the other hand, based on our experience, we see two main factors that discourage candidates from stepping forward:
- Reaching quorum. Lowering the threshold and allowing Security Council members to bypass the Nominee stage can help redistribute votes. The bypass should ideally include a filter, and if the process ever becomes too easy, it can be adjusted. In practice, the member election process already serves as a final filter.
- Running a campaign. Applying, presenting yourself, and showing alignment with Arbitrum voters is demanding and time-consuming, especially for external participants. Extending the time between elections might help motivate more candidates to step forward.
Thanks for bringing this discussion forward and for the dedication on all sides to reach the best possible solution.
RE: 2 Year Terms 
As a current member of the security council and an active delegate that I haven’t experienced fatigue with yearly votes. That said, I don’t see any issue with moving to a 2 year term as long as people can resign. I also don’t mind a 1 year term, it really doesn’t matter, but I mildly support 2 year terms as it reduces operational overhead.
RE: Reduce qualification threshold 
I don’t support reducing qualifications. I don’t see why we would make th upfront filter weaker. Requiring 0.2% of the votable ARB supply, (around 8 to 9 million ARB), feels right. If someone can’t reach that in the nomination phase, they won’t make it as a member anyway. With 6 seats and around ~200 million ARB on average participating, it should be fine…
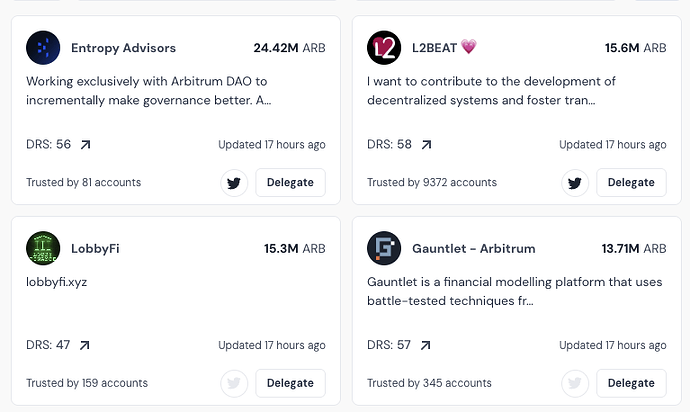
Presented another way, looking at the current top delegates:
With a 0.2% voting threshold, Entropy can make almost 3 full nominations, L2beat and LobbyFi can make almost 2 and Gauntlet can make 1.5 nominations
If we halve the requirement, then Entropy can make almost 6 full nominations, L2beat and LobbyFi can make almost 4 and Gauntlet can make 3 nominations…
Which sounds better? To me it’s an obvious choice, so i don’t support this change.
RE: Bypassing Nominee Selection 
As a current member I am naturally biased, but allowing sitting members to bypass the nomination phase makes sense to me. If you’re already in, and you want to do it again, you’ll almost certainly clear nominations anyway, so forcing it just wastes time. I’m confident no current member would have trouble passing the filter, so why make them jump through the hoops?
RE: Key Rotation for Candidates  & Key Rotation for members
& Key Rotation for members 
Key rotation is obviously critical for members of a 9/12 multisig. People can lose access to their keys in a multitude of ways so having an easy way to fix this issue is a no brainer… but allowing candidates to rotate extra keys feels like unnecessary overhead. Just let members rotate their own keys, nothing more. It is a 9 of 12 multisig, one wrong key for a day doesn’t break it. Adding complexity for the small period where a candidate needs to change their key seems like needless scope that adds needless risks of bugs or exploits. I would suggest to keep it simple, only members can rotate out of their keys, the function for candidates is needless overhead as we can use the fact that members can rotate to address the issue.
We supported nearly the full set of proposed changes in this snapshot, with the exception of “Allow members to bypass Nominee.”
Extending cohort terms and lowering entry thresholds both feel like sensible steps to keep governance stable while also opening the door to a wider pool of candidates. Likewise, adding rotation mechanisms strengthens accountability and reduces key-person risk, an important safeguard as the Council matures.
Where we differ is on skipping the Nominee stage for sitting members. Even experienced members benefit from re-establishing their mandate with the DAO, and the suggested shortcut doesn’t strike us as necessary.
Blockworks Advisory supports this proposal on Snapshot.
Cohort duration increases, lowering the qualifying threshold, the addition of the security council bypass, etc, all seem to bring a very tangible benefit to the election process.
We have voted “none”.
As we mentioned above and as I also explained during the dedicated call, we believe this proposal is not well prepared, and we should go back to the drawing board and discuss it further. Below are our thoughts and comments on individual issues raised in the Snapshot:
- Increase cohort duration - we would be supportive of this point, but only if we are certain that the election process is helping select good candidates. We don’t think this is the case right now, so extending the term without improving the process first could cause more trouble.
- Reduce qualification thresholds - we don’t fully understand the rationale behind this change. Yes, the threshold requirements increase due to unlocks, but the active voting power has been growing lately as well (and it needs to grow further with time anyway to meet the constitutional quorum threshold). Furthermore, progressing security council members would lead to having 6 pre-qualified candidates automatically, and we don’t need much more than that. Especially, that Arbitrum Foundation itself mentioned in the other discussion on that topic that one of the issues with attracting good candidates is that: “We believe that previous candidates who were not elected (some of whom applied multiple times) may have been discouraged from applying again.” We can only select 6 candidates per cohort, so any surplus of good candidates above this threshold is likely to burn out after elections. We want to keep this surplus high enough to have a choice, but low enough not to discourage too many good potential candidates from applying next time. One way of addressing the issue at hand would be to provide some compensation for qualified candidates who were not elected, so that they don’t feel they wasted their time running in the elections. We feel that raising the quorum is not solving anything.
- Progress Security Council members - similarly as with the first point, we would be supportive of this change if we had more trust in the process overall. With the proposed changes, it could be the case that promoting previous security council members without having them go through qualifications could result in reducing their chances of being elected. This is because other candidates will expose themselves during qualifications, and previous members won’t. If even a small portion of delegates just follow their initial choice from qualifications, past members have a lower chance of being elected overall.
- Security Council key rotation - we agree to this change overall, but as explained during the call, we believe this requires some offchain procedure that would ensure (and inform the community) that those key rotations are indeed planned. Right now, the proposal only states that the Foundation will monitor those changes, but does not require public announcements of those changes.
- Changes to the ArbitrumDAO Constitution - as mentioned during the call and in the discussion, we believe that changes in the constitution, even if narrowed down to the security council only, should be considered more broadly.
We will soon join the discussion in the other thread.
Thanks for the proposal.
The only thing I cannot understand is why and how the reduction of the threshold will help. For now, I will not vote for it, although I will continue to observe the discussion and pay close attention.
gm, I voted and supported most of the options.
The part I’m not on board with is skipping the Nominee phase for existing members. With the threshold already lowered, I believe the process is already simple enough. Letting everyone start from the Nominee phase keeps things clearer and puts everyone on the same field.
That said, I agree with L2 that a broader review of the Security Council mechanisms will be necessary in the long run.
Thanks
I have voted as follows:
- Against the longer cohort durations. While I appreciate thinking of voter / canidate fatigue, I agree with @paulofonseca that if we paid openzeppelin to do a study on this we should factor in their opinions. As they are an expert in this field. Plus, this seems purely for just making things easier for voters / candidates and not really for security reasons. Realistically, voting twice a year isn’t that big of an ask, especially now that voting activity has decreased overall. And campaigning is still only a yearly thing.
- I am fine with adjusting the qualification threshold as realistically DAO activity will decrease over time making it harder to reach threshold. So voting for that. Plus if the goal of the qualification is just to check competence, the real limiter should just be the yes/no of the DAO. If we limit too much, were essentially having a mini election before the real election which seems redundant
- However, I disagree with automatically progressing secuirty council members. The vetting process is important, and while presumably a member whose already on the council has met this threshold, I’d prefer in the interest of security to maintain that.
- Security Key Rotation - Yes to members, no to candidates. I essentially agree exactly with @Griff. For the multisig of elected members it’s needed as members may lose access to keys. If they are vetted, elected and in the council the negative security aspects of a lost key far outweigh any minuscule security improvement by not allowing it to be rotated. For candidates, the voting process is relatively short and feels unnecessary to allow key rotation at that stage. Plus, I think there is the very practical answer here - if a candidate really needed to change their keys, they can just do so once they are a member.
I voted for all other options, except this one.
I want to reinforce the question I asked in the GRC regarding the support each option had, with the concrete example from the vote:
Bypass Nomination Phase (the least voted option) had fewer than half of the votes of Increase cohort durations, clearly showing a lack of support.
What will be the method AF will use to apply this feedback? This was not clear in the vote.
The temperature check for this proposal has concluded. Thank you to those who voted.
The results illustrate that there is strong support for:
- Increasing the cohort duration from 1 year to 2 years
- Allowing members to rotate their keys during the term
- Reducing the qualification threshold to progress from the nominee selection
The results reflect less support for:
- Allowing candidates to rotate their keys during the election cycle
- Allowing re-applying members to bypass the nominee selection
We will soon be hosting additional governance calls to further discuss these (latter) changes, before deciding how to proceed with the Tally proposal.
Regarding the point “Allow members to bypass Nominee” there is the following question:
- why is there such a nomination procedure at all?
- why not do a direct vote right away? What is the main point?
If someone thinks that if we make two stages, it will filter out spam, but in fact this just adds work to the delegates, who could also choose the winners at the first stage
In this regard, it is unclear why this parameter scored less than 50%, because this stage is not needed at all
The following reflects the views of GMX’s Governance Committee, and is based on the combined research, evaluation, consensus, and ideation of various committee members.
Committee discussion:
-
Cadence: Clarified that with two staggered cohorts, elections currently occur twice per year. Extending terms to 2 years consolidates to one annual election. The committee supports this change for efficiency and reduced voter fatigue.
-
Threshold: Support lowering to 0.1% to broaden the candidate pool and reduce whale-gating.
-
Member key rotation: Strong support as it improves operational resilience.
-
Candidate key rotation: Concerns raised about unnecessary risk — candidates should demonstrate key control prior to nomination.
-
Incumbent bypass: Opposition due to risk of inflating the ballot and weakening accountability. The new 2-year cadence already reduces burden without needing auto-progression.
Final position (GMX response):
-
 Support: Annual cadence, lower threshold, member key rotation.
Support: Annual cadence, lower threshold, member key rotation. -
 Oppose: Candidate key rotation, incumbent bypass.
Oppose: Candidate key rotation, incumbent bypass.
Rationale (for Snapshot comment):
GMX Governance Committee supports the reforms that strengthen the Security Council process, namely moving to annual elections, lowering the nomination threshold to 0.1%, and enabling mid-term key rotation for members.
We oppose candidate key rotation (as it introduces unnecessary risk) and incumbent auto-bypass (which weakens accountability and inflates ballots). On balance, these targeted changes improve efficiency and resilience while preserving healthy competition in election
well… it depends on how we define “strong support”
for example, I don’t agree that 120.5M ARB casted on the Reduce qualification threshold option should be considered “strong support” because at the time of this offchain vote, the 3% quorum was 139,253,514 ARB and this option didn’t reach that, so I wouldn’t consider it to have had “strong support” on this vote.
it’s cleaner to consider that the options that should move forward are the ones that had more than 3% quorum of support, aka:
- Increasing the cohort duration from 1 year to 2 years
- Allowing members to rotate their keys during the term
As a member of the March 2025 Security Council cohort I am not keen on extending my mandate.
The change can be designed to trigger so that elected members have 2 year mandates after the March 2025 cohort finishes their term.
As mentioned, we will be hosting the Security Council Election Process Improvements proposal: Open Discussion #2 on Friday, October 10th at 13:00 UTC.
The call will be used to further discuss the proposed changes, before deciding how to proceed with the Tally proposal.
In the current system, a rotation takes effect only if 9 of the 12 Security Council members co-sign it. Under the proposed change, any single Security Council member could initiate a rotation independently. However, the Security Council would retain the authority to veto the rotation within the 18-day timelock if it fails to comply with standard procedures (e.g., prior notification to the Security Council and AF, successful completion of compliance checks, etc.).