As one of the Research Members of the ARDC V2, Castle Labs (@CastleCapital), assisted the Risk Member, Nethermind (@Nethermind), in exploring the viability of governance attacks in Arbitrum.
The Supervisory Council requested a comprehensive deliverable that explored the feasibility of a governance attack under the current quorum and analyzed the risks and implications of potentially reducing that quorum. The analysis should attempt to create a framework for how the DAO should think about governance attack risk covering the effects of upcoming token unlocks on ARB distribution and governance security, what the ROI of a governance attack could be, and other topics of this nature. This research should empower the DAO with the insights needed to make an informed decision on whether to adjust quorum requirements. It should also inform the prioritization of ARB staking or similar protective strategies to bolster governance security.
The research was separated into two parts:
- Part 1: Arbitrum Governance and its Challenges – led by Castle Labs – intended to explain and analyse Arbitrum’s governance framework and proposal lifecycle, as well as highlighting historical governance attacks across the industry, and potential risks to the DAO’s decision-making integrity.
- Part 2: Governance Risks Analysis – led by Nethermind – intended to to provide a clear, data-driven view of governance health, focusing on the potential cost of governance attacks, and an analysis on Arbitrum’s quorum.
You can find Part 2: Governance Risks Analysis published here.
Below you will find the full publication of Part 1: Arbitrum Governance and its Challenges, included as collapsible sections.
1. Introduction
Governance is a fundamental component of DAOs, enabling token holders to influence decision-making processes that shape the protocol’s future. In the case of Arbitrum, governance plays a pivotal role in ensuring the stability, growth, and security of the ecosystem.
Arbitrum DAO operates as a decentralized decision-making body where governance power is vested in $ARB token holders. Governance decisions impact the entire Arbitrum ecosystem, including Arbitrum One and Arbitrum Nova, allowing token holders to propose, vote, and implement changes that dictate protocol upgrades, treasury allocations, and operational modifications.
Arbitrum’s governance framework follows a token-based voting model (1 token 1 vote), executed through on-chain smart contracts on Arbitrum One. This structure grants decision-making authority to $ARB holders, who can either vote directly or delegate their voting power to trusted representatives (delegates). While the governance framework promotes decentralization and inclusivity, it is not without challenges. The system must address concerns related to security vulnerabilities, participation rates, centralization risks, and governance capture, which have plagued other DAOs in the past.
This section of the research provides a comprehensive explanation and analysis of Arbitrum’s governance framework and proposal lifecycle, highlighting historical governance attacks across the industry, and potential risks to the DAO’s decision-making integrity. Additionally, we evaluate how other protocols manage similar issues and propose security enhancements to fortify Arbitrum’s governance against known attack vectors.
2. Core Features of Arbitrum Governance
2.1 Governance Components
Arbitrum’s governance structure incorporates multiple components to ensure transparency, accountability, and efficient decision-making. The primary governance elements include:
- ERC-20 Governance Token ($ARB)
- The leading utility of the $ARB token is participation in governance.
- Grants voting rights proportional to the number of tokens held or delegated.
- Tokens are minted on Arbitrum One and are used to govern multiple chains in the ecosystem.
- Holders can vote directly or delegate voting power to representatives.
- Delegation System
- Token holders can delegate voting power to representatives, ensuring broader participation in governance.
- Encourages specialization, where informed delegates make decisions on behalf of less active voters.
- Facilitates governance efficiency by reducing reliance on direct voter participation.
- Need to achieve a balance between broader participation and centralization of voting power
- Security Council
- A 12-member emergency task force, elected semiannually by the DAO.
- Tasked with responding to critical security threats and implementing necessary protocol adjustments.
- Can deploy emergency patches and prevent protocol-level exploits.
- The Constitution
- A foundational document that defines the rules and operations of the Arbitrum DAO.
- It can only be amended through Constitutional Proposals, which require a higher quorum threshold to ensure significant consensus before changes are enacted.
- Guides decision-making processes and serves as the governance framework.
- Quorum Requirements
Different proposals within the DAO have different quorum requirements.
- Constitutional Proposals: Require the participation of at least 5% of votable tokens to pass.
- Non-Constitutional Proposals: Require at least 3% of votable tokens to participate to pass.
- These thresholds ensure that governance decisions have broad community backing before implementation.
- Prevents governance attacks where few active participants could force changes without adequate oversight.
2.2 Proposal Types and Lifecycles
An Arbitrum Improvement Proposal (AIP) is a proposal submitted by a member of the Arbitrum DAO that proposes a change to the Arbitrum ecosystem. There are two types of AIPs:
- Constitutional AIPs: Modify the text or procedures of the Constitution or AIP-1, install or modify software on any chain, or take any action that requires “chain owner” permission on any chain.
- Non-Constitutional AIPs: All other AIPs, such as those that request funds/grants or provide general guidelines or information to the community.
Each proposal follows a structured lifecycle that ensures proper evaluation, discussion, and implementation. While both proposal types share a common foundation, Constitutional AIPs involve additional steps to maintain governance integrity.
Proposal Lifecycle
Phase 1: Temperature Check (Optional, 1 Week)
- A proposed AIP is submitted to the Arbitrum DAO governance forum following a defined procedure.
- A discussion is initiated on the forum to gather community feedback.
- After iterating on the proposal’s comments, a Snapshot poll is created to gauge the interest of Arbitrum DAO members. This poll can only be initiated by an address representing at least 0.01% of the votable tokens.
- The poll runs for 7 days and is decided by a simple majority without a required participation threshold.
Phase 2: Formal AIP Submission and Call for Voting (3 Days)
- The AIP is officially submitted via governance smart contracts on the Arbitrum One chain.
- The proposer must have an address representing at least 1,000,000 votable tokens.
- There is a 3-day period for interested parties to discuss the proposal and gather votes before a voter distribution snapshot is taken.
- The AIP must be labeled as either Constitutional or non-Constitutional and clearly specify which Arbitrum DAO-governed chain(s) it will affect.
Phase 3: On-Chain DAO Vote (14-16 Days)
- Members of the Arbitrum DAO can vote directly on-chain for or against the submitted AIP.
- For the AIP to pass:
- More Votable Tokens must vote in favor than against.
- A certain percentage of all Votable Tokens must vote in favor (5% for Constitutional AIPs and 3% for Non-Constitutional AIPs, referred to as “Threshold 2”).
- The voting period ends 14 days after it starts, but is extended by 2 days if Threshold 2 is reached within the last 2 days.
- If the AIP fails to pass, the process ends here.
For Constitutional AIPs Only (Additional Phases 4-6)
Phase 4: L2 Waiting Period (8 Days for Constitutional AIPs)
- After a Constitutional AIP passes Phase 3, there is an 8-day waiting period before upgrades to the smart contracts occur.
- During this time, those who disagree with the AIP have the opportunity to withdraw their funds or take other necessary actions before the changes take effect.
Phase 5: L2-to-L1 Message (1 Week)
- An L2-to-L1 message is sent to indicate that the Constitutional AIP has passed.
- This message is finalized on L1 (Ethereum mainnet), which takes at least 1 week.
- This ensures that the DAO’s decision is immutably recorded on Ethereum’s base layer.
Phase 6: L1 Waiting Period (3 Days)
- After the decision is recorded on L1, there is a 3-day waiting period to ensure that any in-progress transactions on Ethereum mainnet can finalize before the AIP is implemented.
Final Phase: Implementation
- This is the final step where the approved AIP is fully executed and implemented.
- Once implemented, the changes remain in effect until another AIP is passed to modify them.
Optional Additional Waiting Periods
Proposal submitters may optionally specify an extra waiting period for AIPs that could cause “breaking changes” to allow stakeholders time to adjust before implementation.
Key Stakeholders: Owners of downstream dependencies and the broader Arbitrum ecosystem who need time to prepare for significant changes.
Typical Timelines for Proposal Execution
On average, Non-Constitutional AIPs are 10 days faster to execute compared to Constitutional AIPs:
- Constitutional AIPs: Typically take 37 days from the start of the temperature check to full implementation.
- Non-Constitutional AIPs: Typically take 27 days from the start of the temperature check to execution.
2.3 Delegating Voting Power in Arbitrum DAO
Delegation allows $ARB token holders to participate in governance by assigning their voting power to a trusted representative. This ensures decisions are made by informed and active participants, even if token holders cannot vote on every proposal.
Becoming a Delegate
To become a delegate, contributors must create a profile on Tally and are encouraged to submit a delegate statement on the Arbitrum DAO governance forum. This helps establish credibility and communicate their governance priorities to potential delegators.
Roles and Responsibilities
Delegates are responsible for:
- Voting on proposals and engaging in governance discussions.
- Acting in the DAO’s best interests with transparency and accountability.
- Understanding Arbitrum’s governance framework, including the Constitution.
- Maintaining an active presence in the community and providing a rationale for their votes.
Who Can Be a Delegate?
Any $ARB holder can become a delegate and seek voting power from others. Ideal candidates should:
- Have a strong understanding of Arbitrum and Ethereum governance.
- Commit to consistent participation and informed decision-making.
Delegation enhances governance by ensuring voting power is used effectively, keeping Arbitrum transparent, decentralized, and resilient.
Delegate Voting Power Mapping
Arbitrum currently has a total of:
- 84,565 delegates
- 435,926 delegators
- 330M delegated $ARB (25% of the total $ARB in circulation)
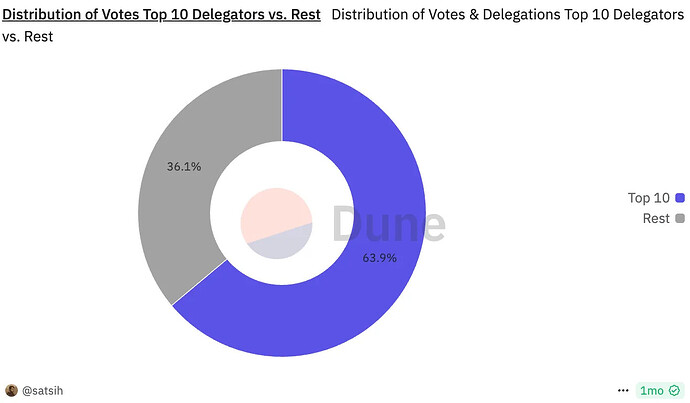
- The top 10 delegates control 63.9% of all the net votes and delegations.
Delegate Participation in Voting
Delegates currently have a participation rate of 1.68% (5-proposal MA).
Voting Power Distribution
This is a snapshot of how the votes are distributed among the top 10 and top 50 delegates compared to all votes.
Top 10 Delegates
Top 50 Delegates
Voting Power of Delegates
Delegate Voting Power Trend
2.4 Quorum Requirements
For proposals to pass in Arbitrum governance, the number of favourable votes must be greater than the unfavourable ones and must meet the participation thresholds:
- Constitutional Proposals: Require at least 5% of all votable tokens to participate
- Non-Constitutional Proposals: Require at least 3% participation of all votable tokens
These quorum requirements ensure that decisions have sufficient community backing before implementation.
The term “votable tokens” refers to the total supply of $ARB tokens, excluding those tokens that have been delegated to the Exclude Address (0x00000000000000000000000000000000000a4b86). This exclusion prevents the quorum requirement from being artificially inflated by tokens that are not intended to be voted. The Arbitrum DAO Treasury is the primary user of this excluded address, but many DAO operational multi-sigs are also encouraged to delegate to this address (e.g. the Multisig Signer Service).
3. Governance Attacks: Lessons from Historical Exploits
Governance attacks exploit structural weaknesses in decentralized decision-making, leading to financial losses, community distrust, and lasting reputational damage. These attacks often stem from low voter participation, sudden shifts in delegation, flash-loan-enabled vote inflation, and poorly designed proposal vetting. This section draws on case studies from Compound, Beanstalk, Tornado Cash, MakerDAO, Steemit, and Build Finance to understand the attack surface and inform Arbitrum’s defense strategies.
Each case is assessed for its governance components targeted, attacker profiles, tools and conditions used, and downstream impacts on governance integrity. We also provide specific lessons for Arbitrum’s current framework, with consideration of how such exploits could occur under its Constitution, delegate structure, proposal lifecycle, and quorum mechanisms.
3.1 Compound Finance (July 2024) — Coordinated Delegate Takeover
In July 2024, Compound narrowly avoided a governance takeover attempt when an anonymous actor known only as “Golden Boys” orchestrated a sudden delegate surge and submitted Proposal 247, which aimed to divert 5% of the treasury to an unknown multisig. Although the proposal appeared out of nowhere with no prior community discussion, it passed initial eligibility requirements due to the rapid acquisition of delegation power. The attack was stopped after real-time alerts and community mobilization, but it exposed key vulnerabilities in delegate transparency, cooling-off periods, and treasury oversight.
Governance Components Targeted
- Delegation System: Relied on a lack of delay in governance power activation. This allowed large amounts of COMP to be delegated rapidly to an unknown actor without friction or visibility, effectively enabling a stealth governance capture.
- Proposal Threshold Access: The attacker used this sudden voting power to meet the minimum threshold for proposal submission, bypassing any requirement for forum vetting or social legitimacy.
- Treasury Governance: The proposal targeted a direct treasury transfer—without requiring a specific rationale or spending plan—revealing the absence of spending caps or formal treasury oversight structures.
Potential Impact
- Would have resulted in an unauthorized diversion of ~5% of DAO funds with little recourse.
- It would have normalized the use of opaque delegate coordination as a path to extracting value from governance, discouraging organic participation.
- Could have triggered secondary proposals that progressively hollowed out treasury oversight norms.
Likelihood in Arbitrum
- Moderate to High. Arbitrum has no enforced delegate registration, no cooldown on newly delegated tokens, and no gating mechanisms for proposals that exceed certain financial thresholds. As a result, an entity able to quickly aggregate 1M ARB—whether through direct holdings or off-chain coordination—could feasibly reproduce this tactic.
3.2 Beanstalk (April 2022) — Flash Loan Governance Attack ($182M Stolen)
Beanstalk suffered one of the most devastating flash loan-based governance attacks in DeFi history. In April 2022, an attacker used a flash loan to gain temporary control of over 79% of voting power and pass a malicious proposal under the guise of humanitarian support. The attack revealed how immediate execution and the lack of guardrails in the voting system enabled catastrophic loss. Despite its simplicity, the proposal bypassed all scrutiny due to protocol-level weaknesses and triggered a full protocol collapse.
Governance Components Targeted
- Voting System: The protocol allowed governance rights to be exercised immediately upon holding tokens, with no requirement for long-term alignment or exposure to protocol risk.
- Proposal Execution: No delay, vetting, or separation between the vote passing and execution allowed malicious logic to be executed before anyone could react.
Potential Impact
- Drained all on-chain funds in a single transaction.
- Eliminated protocol solvency, which caused a depeg and collapse in user confidence.
- Demonstrated that even proposals wrapped in socially beneficial messaging (e.g., aid to Ukraine) could be weaponized.
Likelihood in Arbitrum
- Low. While Arbitrum has similarly unguarded governance rights—any token holder may vote—the attacker would still need to source or borrow over 127M ARB, or buy it outright. Even at suppressed prices, the cost, slippage, and liquidity fragmentation across exchanges and L2s make it a low-return, high-coordination operation. Flash loans could be used to temporarily spike governance power, but the on-chain quorum requirement creates a higher baseline for exploitation.
3.3 Tornado Cash (May 2023) — Self-Destructing Contract Exploit
Tornado Cash was exploited via a sophisticated contract morphing attack. The attacker submitted a proposal containing benign logic, which passed governance review and vote. However, using SELFDESTRUCT and CREATE2, they replaced the contract with malicious bytecode that allowed them to mint $4 million in governance tokens. The attacker later reversed the damage, but the exploit raised critical concerns about bytecode integrity and the reliability of post-vote execution. It underscored the need for stricter proposal and execution controls.
Governance Components Targeted
- Proposal Lifecycle: Relied on a governance pipeline that allowed submission and execution of on-chain logic without verifying that the deployed contract post-vote matched what had been audited or reviewed.
- Smart Contract Approval Mechanism: No checksum or pre-commit hash validation meant that the attacker could use on-chain primitives to alter behavior post-approval.
Potential Impact
- Enabled minting of new governance tokens and direct treasury drain.
- Significantly undermined trust in the technical integrity of governance.
- Introduced uncertainty around how to verify the fidelity of governance proposals and their implementation.
Likelihood in Arbitrum
- Moderate. Although Arbitrum has a clear governance framework and uses predefined AIP templates, the DAO lacks bytecode verification mechanisms or formal audit checkpoints that prevent proposal logic from changing post-approval. Without stricter tooling—such as pre-execution contract validation or standardized deployment paths—Arbitrum could be vulnerable to similar contract morphing exploits.
3.4 MakerDAO (January 2022) — Borrowed Voting Power Attempt
In early 2022, Justin Sun attempted to sway a MakerDAO vote by borrowing MKR tokens from Aave and using the temporary voting power to support the inclusion of TUSD as a collateral type—one that he was commercially aligned with. Though the proposal failed due to public pushback, the incident spotlighted the risk of vote renting, flash governance, and the disconnect between voting weight and economic alignment. It contributed to the ongoing debate about the merits of vote staking and token lockups.
Governance Components Targeted
- Quorum System: Treated all MKR equally, regardless of how it was acquired, allowing large-scale vote influence through short-term lending.
- Token Lending Markets: Introduced a governance arbitrage pathway where actors could borrow influence at minimal cost and reshape strategic parameters.
Potential Impact
- Could have restructured Maker’s collateral base and introduced governance capture by a commercially interested party.
- Would have set a precedent for repeated vote buying in response to liquidity opportunities.
- Long-term, it would deter community-led governance and replace it with mercenary capital.
Likelihood in Arbitrum
- Low to Moderate. ARB is more widely distributed and volatile than MKR, making borrowing 127M ARB difficult and likely to be flagged. However, if leveraged in coordination with other strategies—like rapid delegation shifts or flash loans—borrowing ARB could still play a supporting role in a broader attack. This makes it less likely to be the sole vector, but still relevant as part of a composite strategy. and volatile token, and borrowing 127M ARB would not only be expensive but likely visible via governance monitoring tools. The economic feasibility of renting a governance majority—especially given Arbitrum’s large treasury and the scrutiny around whale behavior—makes this scenario more of a theoretical concern unless lending markets evolve to enable ARB-leveraged governance participation at scale.
3.5 Steemit (March 2020) — Exchange-Controlled Vote Takeover
In 2020, following Justin Sun’s acquisition of Steemit Inc., the protocol experienced a hostile takeover. Sun coordinated with exchanges like Binance, Huobi, and Poloniex to use customer-deposited STEEM to vote out existing witnesses and install his own. The move led to a fork (Hive) and permanently damaged Steem’s credibility. This attack demonstrated how centralized exchanges holding voting tokens on behalf of users can unilaterally subvert decentralized governance when no safeguards are in place.
Governance Components Targeted
- Voting Infrastructure: Permitted token custodians (CEXs) to exercise governance rights over funds they did not beneficially own.
- Validator Elections: In DPoS models, large pools of voting power can rapidly replace consensus nodes without recourse.
Potential Impact
- Steemit underwent an effective governance coup that removed long-standing witnesses and replaced them with hostile actors.
- Triggered a community-led fork (Hive) and reputational damage that permanently fractured the ecosystem.
- Sparked debates on the role of custodians in decentralized systems.
Likelihood in Arbitrum
- Medium. While Arbitrum doesn’t run validator elections in the same way, custodial voting power is significant—especially among passive holders who delegate through aggregators or exchanges. If multiple CEXs acted in unison or were incentivized to vote on behalf of token holders, it’s possible for them to reach quorum and pass a hostile proposal. Arbitrum’s lack of per-address participation caps or CEX monitoring heightens this concern.
3.6 Build Finance DAO (February 2022) — Complete DAO Takeover
Build Finance was completely taken over when a malicious actor used a low-turnout governance vote to pass a proposal granting themselves full minting and treasury rights. The attacker went on to mint millions of BUILD tokens, drain ETH, and rug all liquidity—effectively destroying the DAO. The governance mechanism had no quorum, safeguards, or review layers, and the DAO had no emergency powers to recover from the attack.
Governance Components Targeted
- Proposal Gatekeeping: No quorum minimums or social review processes allowed a hostile actor to capture control without opposition.
- Token-Voting System: Unchecked token-based voting made the governance system brittle in low-turnout environments.
Potential Impact
- Resulted in the total loss of Build’s protocol governance.
- Enabled unauthorized minting, treasury draining, and transfer of protocol assets to the attacker’s wallet.
- The DAO never recovered; BUILD token collapsed.
Likelihood in Arbitrum
- Very Low. Arbitrum’s non-Constitutional AIPs still require 127M ARB to meet quorum, which is impossible for a single attacker without massive coordination or token purchase. Participation remains low, but the margin between current turnout and minimum quorum still demands significant voter consolidation. Unless quorum rules are reduced or coordination mechanisms fail, a Build-style hostile takeover is highly unlikely.
4: Governance Attack Scenarios and Their Risk Implications
This section outlines three key governance attack vectors in the Arbitrum DAO, focusing on the specific components of governance that are vulnerable, the severity of their potential impact, and the likelihood of their success given Arbitrum’s current governance framework.
4.1 Flash Loan-Assisted Contract Morphing Attack
Targeted Governance Components:
- Voting System: Exploits the lack of token lockups or holding periods, allowing flash-loaned voting power to influence outcomes.
- Proposal Execution Logic: Manipulates pre-execution contract state using self-destruct and
CREATE2to swap legitimate contracts with malicious ones.
Potential Impact:
- Treasury Drain: Attacker can siphon large amounts of ARB or redirect treasury funds.
- Loss of Governance Integrity: Creates long-term vulnerability to reentry or embedded logic exploits.
- DAO Confidence Collapse: Demonstrates that Arbitrum can be hijacked with temporary voting power.
Likelihood in Arbitrum Today:
- Moderate to High. No current mechanism prevents flash-loan-acquired tokens from being used in governance. The execution delay on non-Constitutional AIPs (14+ days) provides some detection time, but not necessarily mitigation unless an external veto mechanism is used.
- Elevated Risk for High-Value Proposals. Attackers could justify costs if the treasury transfer is large enough to outweigh slippage and flash loan fees.
4.2 Rapid Delegation Exploit: Bypassing the Temperature Check
Targeted Governance Components:
- Delegation System: Governance allows immediate use of newly delegated tokens for on-chain proposal submission.
- Temperature Check Process: Non-mandatory nature allows attackers to bypass community vetting entirely.
Potential Impact:
- Proposal Hijacking: Attackers can introduce harmful AIPs without social consensus.
- Treasury Risks: Funds could be misappropriated before community mobilization.
- Undermines Delegate Legitimacy: Perception of delegate coordination or bribery may reduce faith in representative governance.
Likelihood in Arbitrum Today:
- High. There is no delay between delegation and proposal eligibility. A coordinated delegate campaign or bribe-based aggregation could allow instant proposal creation with 1M+ ARB voting power.
- Easier During Low Attention Periods: Weekend or holiday exploits more likely to avoid scrutiny.
4.3 Emergency Treasury Reallocation Proposal (ETRP)
Targeted Governance Components:
- Proposal Validation and Framing: Lack of robust mechanisms to challenge narrative framing of proposals.
- Delegate System: Heavily concentrated voting power enables small collusions to reach quorum.
- Temperature Check (Optional): Bypassed entirely, leaving no off-chain deliberation.
Potential Impact:
- Large-Scale Fund Theft: Proposal could move tens of millions of ARB under plausible-sounding pretenses.
- Market Instability: Token price crash from rapid treasury sales.
- Governance Crisis: Reveals how quickly and quietly Arbitrum can be compromised.
Likelihood in Arbitrum Today:
- Moderate. Would require coordination across a few top delegates (top 5 control ~40% of vote share). Given current quorum (~127M for non-Constitutional AIPs), collusion or bribery with a few large delegates is a feasible threat vector.
- Higher if Security Council does not act: No formal veto mechanism exists outside of proposal failure by vote.
4.4 Additional Risks to Monitor
Security Council Infiltration
- Targeted Component: The 12-member Security Council can bypass normal governance in emergencies. It is elected semiannually via standard delegate voting.
- Impact: A compromised Security Council could execute emergency actions or fail to act against an exploit.
- Likelihood: Currently low, but increasing with delegate apathy and low participation. Top 5 delegates already have outsized influence, so a small group could coordinate Security Council member selection.
Constitutional Proposal Exploits
- Targeted Component: Arbitrum Constitution and AIP-1 governance rules.
- Impact: If passed, could change quorum requirements, reduce safeguards, or centralize power.
- Likelihood: Very low today, but increasing as votable supply grows and quorum margin erodes. Monte Carlo simulations suggest >95% of constitutional proposals fail at current participation rates, meaning a well-funded attacker with high social coordination could dominate a low-turnout vote.
5. Mitigating Governance Risks in Arbitrum DAO
This section incorporates lessons from both historical case studies and the Nethermind’s Part 2: Governance Risks Analysis, which identified five core governance vulnerabilities in the Arbitrum DAO:
- Low voter participation: Reduces quorum legitimacy and increases the impact of coordinated minorities.
- Concentrated voting power: A small set of delegates control outsized influence, raising the risk of collusion or targeted bribery.
- Lack of voter authentication and transparency: Enables undeclared or proxy actors to exert disproportionate control.
- Minimal deterrents for malicious governance behavior: No slashing, staking penalties, or accountability mechanisms currently exist.
- Insufficient safeguards on proposal execution: Especially for treasury transactions or governance logic changes, increasing systemic risk.
For clearer, data-driven recommendations focusing on the potential cost of governance attacks, and Arbitrum’s quorum, see Part 2: Governance Risks Analysis.
While Arbitrum’s modular governance system enables decentralization and adaptability, it also creates opportunities for manipulation. The following mitigations aim to preserve openness while increasing the DAO’s governance resilience.
5.1 Strengthening Proposal Vetting and Oversight
Weak proposal screening creates openings for malicious activity. To reinforce this phase:
- Structured Proposal Requirements
- Mandate the use of standardized proposal templates including risk disclosures, value impact, and governance rationale.
- Require proposers to pre-commit to code or deployment logic, with checksum verification to detect post-vote modifications.
- Minimum Thresholds for Off-Chain Support
- Implement quorum thresholds in temperature checks or require minimum delegate endorsements prior to on-chain progression.
- Risk Assessment and Audit Layers
- Create a Standing Risk Committee (as proposed by Nethermind) to assess potential governance threats, especially for proposals touching treasury, execution logic, or governance contracts.
- Require third-party audits or automated scanning tools for contracts linked to executable proposals.
- Anomaly Detection Infrastructure
- Introduce automated monitoring of unusual voting or delegation patterns using bots and dashboards.
- Build public alert systems to notify delegates and token holders of outlier governance behaviors.
5.2 Reducing Attack Vectors in Voting
An additional risk identified by Nethermind—and visible in current governance participation trends—is the growing difficulty of reaching quorum as the total votable ARB supply increases. With token unlocks, ARB’s voting denominator expands over time, while actual voter turnout remains stagnant. This creates a governance deadlock risk: well-intentioned proposals may fail not because of opposition, but due to an inability to mobilize sufficient votes. It also increases vulnerability to quorum manipulation, where low activity windows allow a motivated minority to dominate key decisions.
Token-based voting without friction allows flash governance, vote renting, and apathy-driven takeovers.
- Governance Power Lock-In
- Introduce minimum token holding periods (e.g., 7–14 days) before votes become valid, deterring flash loan-based attacks.
- Consider ARB staking mechanisms with unbonding delays to tie voting power to longer-term alignment.
- Participation-Based Safeguards
- Scale quorum requirements to proposal impact. For example, require higher turnout for treasury transfers than for governance ratification.
- Expand the Delegate Incentive Program (DIP) to reach smaller delegates and encourage wider participation.
- Delegate Accountability
- Require rationales for high-impact delegate votes, increasing transparency.
- Mandate delegate profiles and history disclosures (as piloted in Nethermind’s recommendations).
- Mitigate Vote Renting Risk
- Explore quadratic voting or conviction voting models as longer-term adjustments to reduce the influence of short-term token accumulation.
5.3 Refining the Role of the Security Council
Arbitrum’s Security Council can act as a failsafe but requires clearer authority and thresholds:
- Emergency Review Powers
- Empower the Security Council to pause execution on flagged proposals pending risk committee review.
- Formalize a veto mechanism or hold period for high-risk categories (e.g., treasury transfers >$5M, changes to governance logic).
- Time-Gated Execution
- Require delayed execution (e.g., 7 days) on proposals affecting governance contracts or system roles.
- Introduce multi-phase approvals for highly impactful proposals: initial vote, audit, final ratification.
- Community-Sourced Alerts
- Allow delegates and stakeholders to flag proposals that may require Security Council intervention.
While such powers improve protocol safety, they represent a step toward guardianship and may reduce decentralization. A balance must be struck to maintain credible neutrality while enforcing minimum governance security standards.
5.4 Continuous Threat Monitoring and Adaptive Governance
Threats to governance are evolving. Monitoring and adaptation are critical.
- Real-Time Governance Intelligence
- Launch public dashboards for tracking governance movements, delegation flows, and voter concentration.
- Integrate alert systems (e.g., via Discord or RSS) to notify of irregular delegation spikes, proposal timing anomalies, or flash coordination patterns.
- Stress Testing and Scenario Planning
- Run quarterly governance simulations, including attack scenarios involving flash loans, rapid delegation, or hostile quorum manipulation.
- Commission external red teams or researchers to test proposal submission and vote manipulation vectors.
- Policy Refinement and Cross-DAO Learning
- Institute an iterative governance review cadence, drawing on external cases (e.g., Maker, Uniswap, Optimism) to improve Arbitrum’s own policy layers.
- Build modularity into governance logic to allow for rapid proposal threshold or quorum rule changes under defined circumstances.
5.5 Addressing Quorum Fragility from Token Supply Growth
A unique structural risk facing Arbitrum DAO is the increasing difficulty of reaching quorum as the total votable ARB supply expands. As more ARB tokens are unlocked and become liquid, the quorum requirement—currently defined as a fixed percentage of the total supply—effectively becomes more difficult to meet over time, especially if voter turnout stagnates or declines.
- Governance Paralysis Risk
- Critical proposals may fail not due to opposition, but simply due to a lack of mobilized voting power, leading to stalled initiatives and funding bottlenecks.
- Quorum Manipulation by Minority Actors
- Low turnout opens a window for small, well-coordinated actors to pass proposals under the radar, especially during periods of community inactivity.
- Growing Governance Disenfranchisement
- As reaching quorum becomes harder, smaller delegates and average token holders may disengage, believing their votes do not matter—reinforcing low participation loops.
Mitigation Pathways:
- Introduce a dynamic quorum model, where quorum thresholds adjust based on recent voter turnout averages or relative vote engagement (with limits in place for safety).
- Launch a quorum health dashboard, with visibility into current turnout trends, voting gaps, and delegate response times.
- Expand efforts to re-delegate dormant voting power through opt-in systems or pooled delegate initiatives.
5.6 Conclusion: Securing Governance While Preserving Decentralization
Arbitrum DAO must evolve governance protections in parallel with its growth. Based on Nethermind’s findings and lessons from DeFi history, this means:
- Upgrading proposal vetting with structured templates and risk assessments.
- Reducing voting attack surfaces through lock-in mechanisms and participation thresholds.
- Clarifying the Security Council’s authority as a backstop for critical governance events.
- Investing in monitoring and responsiveness to stay ahead of coordinated attacks.
- Expanding re-delegation efforts to help mobilize dormant voting power and reduce the risk of concentrated or stagnant governance.
Each layer of protection should be designed to preserve decentralization, favor community-led security, and ensure that Arbitrum’s governance remains open, adaptable, and resilient.